A report of the malicious JavaScript on robint.us can be seen in this Wepawet report. I noticed that within the JS, the variable name "cuteqq" was used for evaluating the payload - this sounded really familiar. Google "cuteqq malware" and 784 results returned ... CuteQQ is actually a browser exploit toolkit that was popular during 2008. Google for "var cuteqq" and there are several more interesting results including those marked "This site may harm your computer."
Here is a VirusTotal report for an early version of the CVE-2010-0249 ("Aurora") exploit, showing that the malicious binary was authored by the "Cuteqq Software Team"
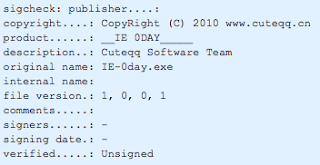
"Cuteqq" does seem to have its usage in several Chinese exploits / variable names. (QQ is a popular Chinese web service for email, chat, news, etc.)
VirusTotal analysis of the actual payloads shows that most A/V vendors (including our inline A/V solution) detect the malicious payloads dropped by the infected webservers:
-
http://www.virustotal.com/analisis/59433694b9b8da6fe723bc15a00e0dc0c4177ea56ac6d8355aa73ad1c6e7d72c-1276095830 -
http://www.virustotal.com/analisis/ebd5fbeae8265f088852a916f221f816caf742d3d2f38e014287ce8a82d6f772-1276202168
Neither of these payloads attributed themselves to the "Cuteqq" team directly within the binary signature / authorship information.
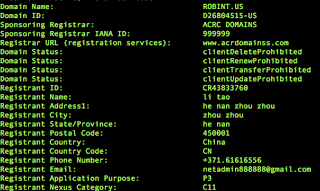
WHOIS information for the two domains related to this incident show CN attribution:
 |  |





