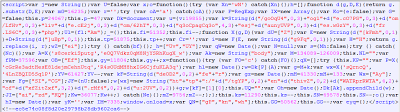
Following on the wave of "iepeers.dll" exploits, we found that the same client IP address involved in the attacks, used an open proxy to reach thousands of pages containing IE6 exploits. These consisted of legitimate sites which had been hacked and the following Javascript code had been injected into the pages:
Obfuscated malicious Javascript
The code is well obfuscated - it is different on each of the hacked sites and uses exceptions and eval functions to break deofuscation tools. The code is obfuscated several times, and does not do any document.write functions, all of which can make the script more difficult to decode. In the end, the script adds an invisible iframe to a Russian (.ru) website on port 8080. The domain name used by the iframe varies.
Fortunately, the author went too far with the obfuscation, and it is actually fairly easy to recognize the obfuscated code. We wrote a few signatures last week to catch sites hijacked with this code. Among the hacked sites, we found that the Philippine Yellow Pages: http://yellowpageph.com/ had been successfully attacked. I have checked several pages on the site and only the home page seems to be infected.
Invisible iframe to tenthprofit.ru:8080
We've seen this malicious code on all kinds of websites, but the URL used on this Yellow Pages site is interesting: hxxp://tenthprofit.ru:8080/google.com/live.com/pagesjaunes.fr.php (the URL is inaccessible at this time). "pagejaunes" is French for Yellow Pages. This may just be a coincidence...
I have contacted the website, it may be cleaned up at the time this post is published.
-- Julien