PPI being pay-per-install ...
This morning I saw some interesting transactions to:
hxxp://promoupdate.info/setup###.exe
where ### are numbers, for example, "519".
MD5: 1568edcd29629f577207d7396646b741
VirusTotal results 8/43 (report), detected as (among other names):
Win32:Hottrend-B
Turns out this is being spread through spammers, SEOers, etc. being financed in a PPI model, something that I have discussed before in the past. This time I have a screenshot to share related directly to the finance aspect of this particular PPI: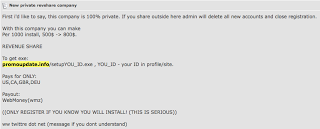
This post was created today. We can see from the PPI ad that those engaging in this particular campaign stand to make between $500 and $800 per 1000 installs (< $1 per install). The numbers in the executable, like "519" correspond to the account for the spammer/SEOer that is monetizing this. Domain: promoupdate.info Whois billing contact shows likely Russian affiliation: 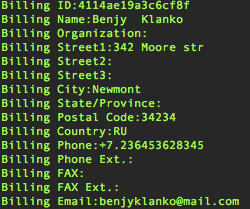 Here is the actual Affiliate Network setup by this guy:
Here is the actual Affiliate Network setup by this guy: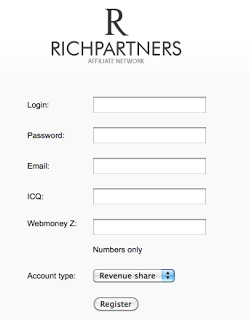 Domain: twittre.net (private/masked Whois)
Domain: twittre.net (private/masked Whois)
(note the RU nameservers)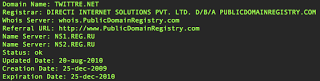 Source of the twittre.net page actual reveals that the Affiliate website is loaded from rich-partners.com:
Source of the twittre.net page actual reveals that the Affiliate website is loaded from rich-partners.com: Domain: rich-partners.com
Domain: rich-partners.com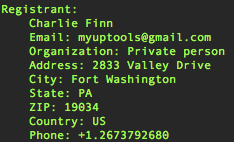 No surprise that the contact details are bogus, but the email address is legit, here's a past domain registered with these email credentials:
No surprise that the contact details are bogus, but the email address is legit, here's a past domain registered with these email credentials: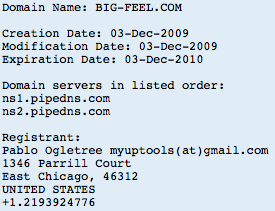 Robtex shows these other domains (all likely other PPI sites) on 91.188.60.10 (Sagade Ltd. <- not a surprise for some) in Latvia, hosting promoupdate.info:
Robtex shows these other domains (all likely other PPI sites) on 91.188.60.10 (Sagade Ltd. <- not a surprise for some) in Latvia, hosting promoupdate.info: 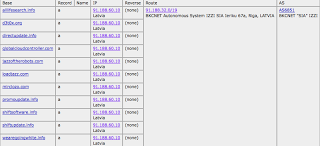
Blog de Zscaler
Reciba las últimas actualizaciones del blog de Zscaler en su bandeja de entrada
SuscribirseNew PPI Campaign
Gracias por leer
¿Este post ha sido útil?

Reciba las últimas actualizaciones del blog de Zscaler en su bandeja de entrada
Al enviar el formulario, acepta nuestra política de privacidad.




