One of our blog readers, Mr. Jon Leathery informed me yesterday about a link in a Google News search leading to a malicious website. “Laurence Fishburne leaving CSI”, was a popular topic recently and was being taken advantage of to spread malware. Here is the screenshot of a Google news search with that term:
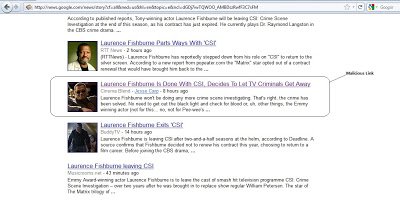 Look at the highlighted news in the image above. If a user clicks on that link, it will redirect them to a malicious website containing heavily obfuscated JavaScript, which will download additional malware onto their system. The user will be only redirected to the malicious website if they are coming from Google News based on HTTP referrer header, a common technique that we see to further obfuscate the attack. Let’s look at the news page:
Look at the highlighted news in the image above. If a user clicks on that link, it will redirect them to a malicious website containing heavily obfuscated JavaScript, which will download additional malware onto their system. The user will be only redirected to the malicious website if they are coming from Google News based on HTTP referrer header, a common technique that we see to further obfuscate the attack. Let’s look at the news page: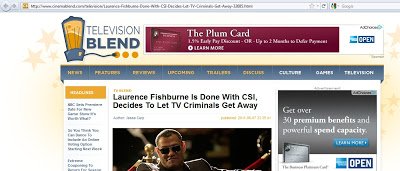 The above news site contains the malicious obfuscated JavaScript code at the top of the page. Here is a screenshot of the source code:
The above news site contains the malicious obfuscated JavaScript code at the top of the page. Here is a screenshot of the source code: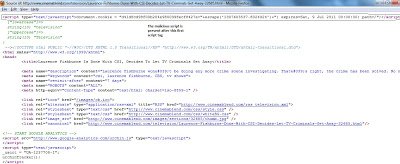 Remember, the malicious JavaScript code is only inserted when the referrer is the Google News site. If you visit this website directly, the malicious code will not be loaded. Here is what the obfuscated JavaScript looks like:
Remember, the malicious JavaScript code is only inserted when the referrer is the Google News site. If you visit this website directly, the malicious code will not be loaded. Here is what the obfuscated JavaScript looks like: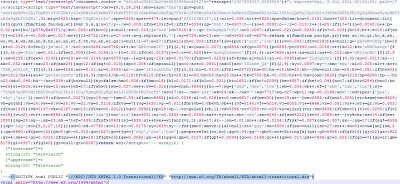 Once decoded, it will reveal a script tag, pointing to a malicious website. Here is the decoded content:
Once decoded, it will reveal a script tag, pointing to a malicious website. Here is the decoded content: The above malicious link then redirects the victim multiple times, finally loading a page containing heavily obfuscated JavaScript code. Here is what the final exploit code looks like:
The above malicious link then redirects the victim multiple times, finally loading a page containing heavily obfuscated JavaScript code. Here is what the final exploit code looks like: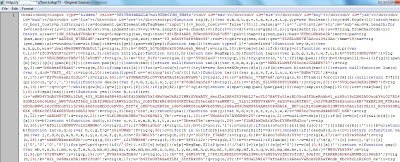 The above code is highly obfuscated with every string randomized. Automated analysis tools failed to decode it and manual analysis was required, which I will explain in a separate blog. The above malicious exploit code exploits various known vulnerabilities to download additional malware on the system. Here is the Fiddler capture of the malicious requests:
The above code is highly obfuscated with every string randomized. Automated analysis tools failed to decode it and manual analysis was required, which I will explain in a separate blog. The above malicious exploit code exploits various known vulnerabilities to download additional malware on the system. Here is the Fiddler capture of the malicious requests: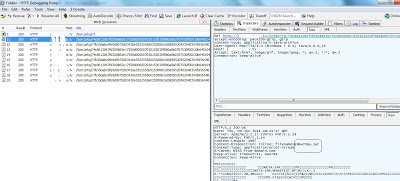 The exploit code downloads multiple malicious JAR files on the system after exploitation. The VirusTotal results remains very poor for one of the malicious JAR files, with only 2 out of 43 Antivirus triggering on it. Fake Antivirus pages also commonly use the technique of checking referrer strings before loading page content. The malicious content is only loaded if the victim is coming from a Google search page. The trust that people place in Google search results is being abused to social engineer victims into believing that malicious search result links are safe. Unfortunately, nothing could be further from the truth.
The exploit code downloads multiple malicious JAR files on the system after exploitation. The VirusTotal results remains very poor for one of the malicious JAR files, with only 2 out of 43 Antivirus triggering on it. Fake Antivirus pages also commonly use the technique of checking referrer strings before loading page content. The malicious content is only loaded if the victim is coming from a Google search page. The trust that people place in Google search results is being abused to social engineer victims into believing that malicious search result links are safe. Unfortunately, nothing could be further from the truth.Be Safe
Umesh





