... or at least be careful if you do.
 Who doesn't like a good episode of Family Guy? Well even if you don't, that isn't the point of this post. There are dangers visiting and trusting sites that link to and embed content into their site without validating the content first. Malware advertisers have been leveraging pop culture content and stories to entice and social engineer their victims into downloading their malware - Michael Jackson's death themed malware is a prime example. This morning I came across some malicious redirector sites that look very much like (and may be) legit sites. None-the-less, when a visitor follows the embedded video link to view their favorite episodes of Family Guy or another show, they would receive an annoying dose of survey pages (i.e., sign me up for spam) and/or malware.
Who doesn't like a good episode of Family Guy? Well even if you don't, that isn't the point of this post. There are dangers visiting and trusting sites that link to and embed content into their site without validating the content first. Malware advertisers have been leveraging pop culture content and stories to entice and social engineer their victims into downloading their malware - Michael Jackson's death themed malware is a prime example. This morning I came across some malicious redirector sites that look very much like (and may be) legit sites. None-the-less, when a visitor follows the embedded video link to view their favorite episodes of Family Guy or another show, they would receive an annoying dose of survey pages (i.e., sign me up for spam) and/or malware.
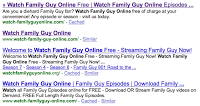
Here's a snippet of such sites for Family Guy:
watch-familyguyonline.com
www.watch-family-guy-online.com
www.watch-familyguy-online.com
watchfamilyguyonline.org
What appears to have happened here is that sites like these automatically embed links to megavideo.com or other external video sources that are tagged as being Family Guy (or other specific) episodes without validating them.
Following the redirects, I tracked these two examples to the following malware:
hxxp://watch-familyguyonline.com/testt/
hxxp://www.watch-family-guy-online.com/season-8/episode-9-business-guy/
The loaded megavideo.com content, eventually taking the path:
- Megaclick.com, e.g., hxxp://s.megaclick.com/ad.code?de=9e09c529-07435895-c974b103-73e05fb5-bd3a-4-a48c&tm=1261149695.21963&du=aHR0cDovL3d3dy55ZXpsaW5rLmNvbS9zdGF0cy5waHA%2fcD1tZWdhY2xpY2tnenVz%0a&api_var_rd_mode=popunder_html
- Yezlink.com, e.g., hxxp://www.yezlink.com/stats.php?p=megaclickgzus
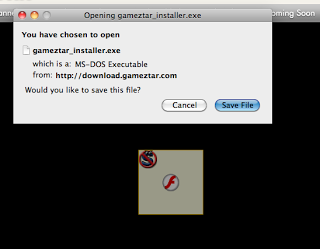
- 302 redirect to hxxp://www.gameztar.com/go.php?a=1839&l=112
- 302 redirect to hxxp://www.gameztar.com/startDownload.do?a=1839&l=112
- Download: hxxp://download.gameztar.com/toolbar/gameztar/download/avatar/2.1.102.r6380/000011_oSz/gameztar_installer.exe
The MD5 of the sample is: c5b8e34abfb067ddc5f294cb057f86a0
With VirusTotal results (9/41): http://www.virustotal.com/analisis/a4b092a2b60a07aa6127314e5fbf37642272ad725569ed008df108fe43fd524b-1261147802
Update:
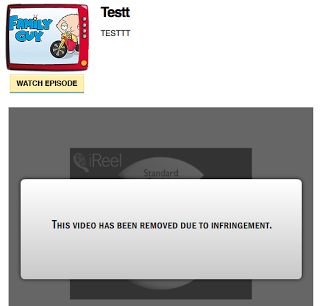
While writing this post, it appears that the first video has already been removed by megavideo (for infringement violation).