Update:
Upon receiving additional file-system information from an infected host, the malware that resulted in being dropped was a TDSS variant, which corresponds to the earlier statement about Rorpian being used as a loader for TDSS. This was pulled from the MBR of the infected:
Executables:
MD5: 57eaccabfa387d51a29b12fb9f2451f1
V/T Report (29/44)
MD5: 73cfb1489b7949cfb9c76fc9c727fb58
V/T Report (26/44)
DLL:
MD5: 4f6ebfe892b1be6c40ea0895c5c51d21
V/T Report (9/44)
Note: the binary has debugging info enable, including reference to its PDB file:
H:\atrohnwA\gqybua\ybgh\qdyy.pdb
(possible phonetic strings - there are other such strings in the binary as well)
The original infection on this host occurred from exploitation of the LNK vulnerability, in order to execute a Rorpian payload:
MD5: 4e69a47a418b7af08f53effd0e8c61b7
V/T Report (28/44)
Original Post:
We've had reports that some systems have had their DNS resolution settings modified to resolve domains from:
188.229.89.121
The IP belongs to a known "bad" /24 netblock in Romania, part of AS43134 (COMPLIFE-AS CompLife Ltd) ... a netblock that we had perviously noted within Scrapbook.
Which in effect, redirects all web browsing attempts to:
hxxp://188.229.89.121
Which presents a screen showing that you need to "Update your browser":
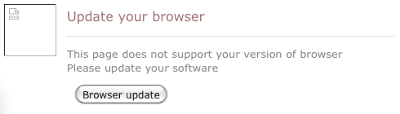 The image file and malware download viewable from my system linked to a placeholder "update.browser.com":
The image file and malware download viewable from my system linked to a placeholder "update.browser.com": At least the attacker has a sense of humor :) the meta tag shows "(C) Bank of Nkolai. Look I have a pen !" -- this is in reference to this very funny awareness ad on cyber crime, see YouTube video.
At least the attacker has a sense of humor :) the meta tag shows "(C) Bank of Nkolai. Look I have a pen !" -- this is in reference to this very funny awareness ad on cyber crime, see YouTube video.The actual malware is live and downloadable from:
hxxp://188.229.89.121/X
A malware report related to this is viewable here:
MD5: 2dff3265278fb6a894829a75f6275c8a
V/T report: 28/44
The malware variant goes by many names: Rorpian, Buterat, Kolab, and SillyFDC. For ease, we'll just call it Rorpian -- which numerous sources describe it as a worm that spreads through network shares, exploits the .LNK vulnerability (MS10-046), and exploits a vulnerability (MS07-029) in DNS Server service (MS Encyclopedia entry). This worm can act as a loader for the TDSS rootkit (reference).
Further check-ins from the infected are made to the 188.229.89.121 c2 with the format:
/slog
&log=startum
&id=[ID number]
&os=[OS version]
&version=1d
&data=
Note: the User-Agent string used in the check-ins was:
Microsoft-WebDAV-MiniRedir/5.1.2600
There have been Internet reports of Mac and Ubuntu systems having this DNS change occurring within their /etc/resolv.conf ... however, this appears to just be a result of infected Windows systems that are setting DNS setting through DHCP for all devices on the network versus this malware infecting Mac/Ubuntu.





